On December 14, 2023, during GMT+8 hours, there was a supply chain breach impacting the Ledger Connect Kit, resulting in a theft of at least $600,000 by attackers.
How and when the attack started?
7:43 PM: @g4sarah on Twitter reported a potential hijacking of Zapper's DeFi asset management protocol front-end.
8:30 PM: Sushi's CTO warned users against interacting with dApps due to a suspected compromise of a commonly used Web3 connector, possibly impacting numerous dApps, and suggested Ledger might contain suspicious code.
8:56 PM: Revoke.cash announced the compromise of several crypto applications, including their own, due to the Ledger Connect Kit library issue, leading them to temporarily shut down their website. Kyber Network also disabled its front-end UI as a precaution.
9:31 PM: Ledger identified and removed a malicious version of the Ledger Connect Kit, replacing it with a genuine version, and advised users not to interact with dApps until further notice.
9:32 PM: MetaMask advised users to enable the Blockaid feature in the MetaMask extension before executing any transactions in the MetaMask Portfolio.
Vulnerability Analysis & Impact:
Details Of the Attack:
Malicious JavaScript code was found in versions @ledgerhq/connect-kit=1.1.5/1.1.6/1.1.7, inserted by attackers. This code replaced typical window logic with a Drainer class, creating a deceptive DrainerPopup and assuming control over asset transfer functions. The attackers exploited this to conduct phishing assaults on cryptocurrency users using a CDN.
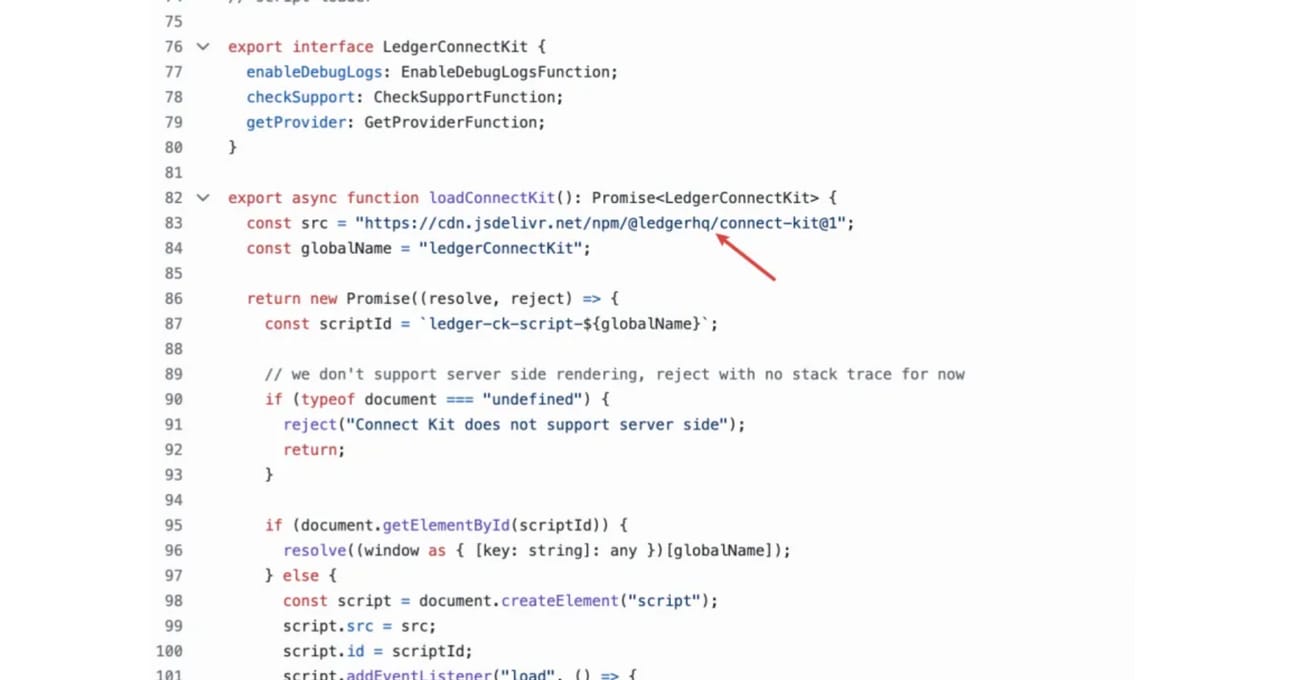
Affected Version :
In the code of @ledgerhq/connect-kit 1.1.5, the attacker made reference to 'Inferno,' a term suspected to be linked to the Inferno Drainer phishing gang notorious for orchestrating multi-chain scams.
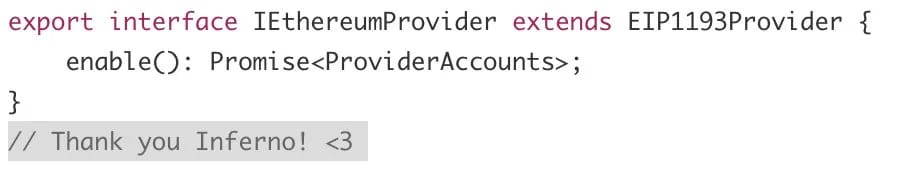
Within the code of @ledgerhq/connect-kit 1.1.6, the attacker included a message and embedded malicious JavaScript code.
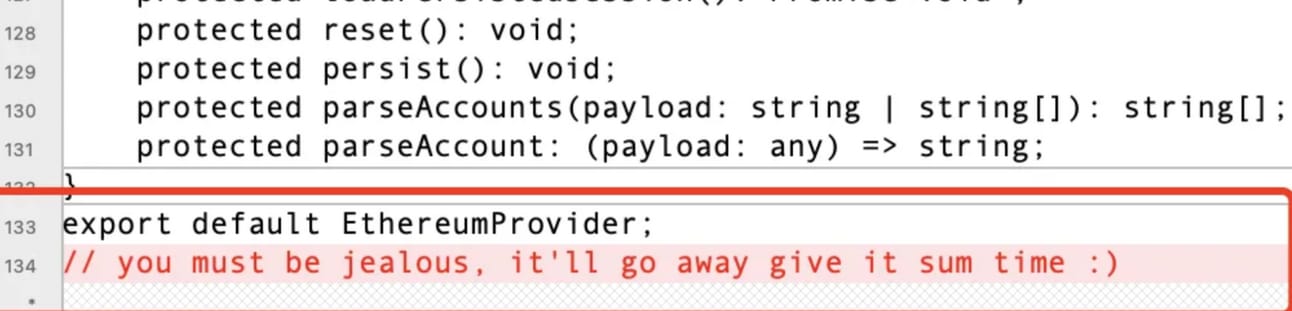
In the code of @ledgerhq/connect-kit 1.1.7, the attacker inserted a message and incorporated malicious JavaScript code.

The Ledger wallet itself remains unaffected, but the breach has major implications for various applications utilizing the Ledger Connect Kit, including SushiSwap, Zapper, MetalSwap, Harvest Finance, and Revoke.cash. The attack grants attackers the ability to execute code at the application's permission level, enabling fund draining without user interaction, widespread phishing, and exploitation of user panic through misleading asset transfers, potentially resulting in asset loss via fake wallet downloads.
Examination of Attack Method
At 11:09 PM, confirmation arrived that a former Ledger employee fell victim to a phishing attack:
The attackers acquired access to the employee’s NPMJS account.
Subsequently, they distributed malicious iterations of the Ledger Connect Kit (versions 1.1.5, 1.1.6, and 1.1.7).
The malevolent code, employing a compromised WalletConnect, rerouted funds to the hackers' wallet address.
In response, Ledger swiftly issued a verified and authentic Ledger Connect Kit, version 1.1.8, strongly recommending immediate updates.
Even after the removal of the tainted Ledger npmjs versions, compromised JavaScript files persist on jsDelivr :
Official sources advise waiting for 24 hours before utilizing the Ledger Connect Kit due to potential delays in CDN updates.
Project maintainers are urged to secure specific versions when deploying dependencies via third-party CDN mirror sources. This precautionary measure aims to mitigate potential risks stemming from malicious releases and subsequent updates, as suggested by @galenyuan.
Acknowledging these recommendations, the official team plans to reevaluate their approach in forthcoming revisions.
Last update from the team :
How does DeHack come into play?
DeHack rigorously assesses many aspects and monitors various events to harden measures against potential hacking dangers inside the Web3 ecosystem. Our priority is to detect flaws that hackers may exploit in advance, ensuring solid security measures within protocols. This proactive approach, along with AI and ML technologies, enables us to protect Web3 systems, reinforcing them against future intrusions and instilling trust in their resilience.
