What happened to Orbit chain?
Orbit Chain became the last exploited DeFi protocol of 2023, experiencing significant financial losses. On New Year's Eve, December 31, 2023, Orbit Chain fell victim to a series of exploits within its transactional infrastructure, resulting in a staggering financial setback of approximately $82 million.

Orbit Chain : An Overview
Orbit Chain is a multi-asset blockchain that stores, transfers, and verifies information and assets which exist on various public blockchains through Decentralized Inter-Blockchain Communication (IBC). Orbit Chain's standard aims to work as a hub for public blockchains, for fluid asset movement and interaction within a single blockchain network.
Check out here for more details.
Vulnerability Analysis & Impact:
Details Of the Attack:
The vulnerability exploited here originates from the misuse of legitimate signatures, enabling unauthorized transactions. It appears the exploiter gained access to the owner's private keys, facilitating the creation of fake signatures to carry out fraudulent withdrawals.
Flow Of the Attack & Fund flow :
Breakdown:
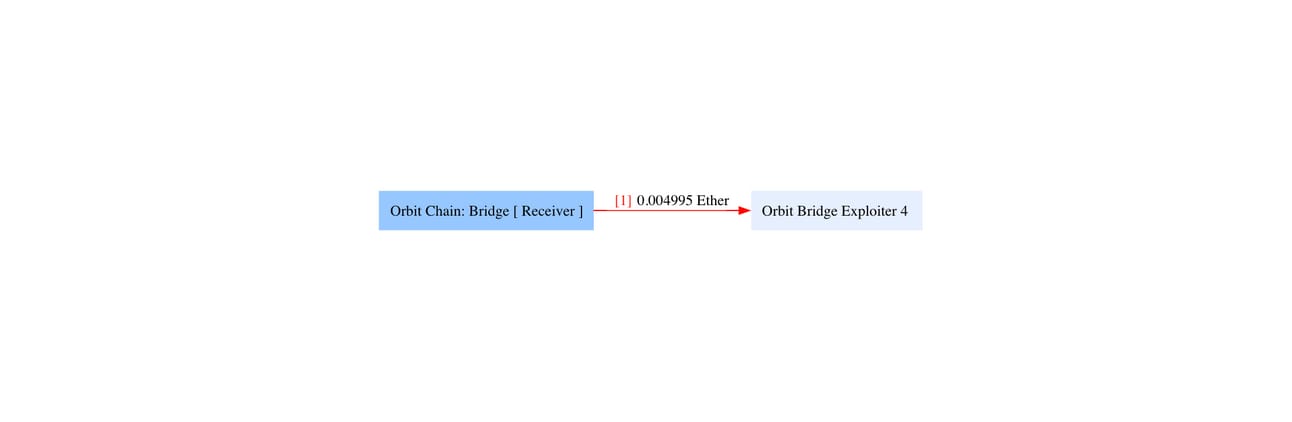
1️⃣ ETH:
At 06:14:11 PM UTC, an address labeled as the Orbit Bridge Exploiter 4 siphoned 0.004 ETH from the Orbit Chain ETH vault. Shortly after, at 07:45:59 PM UTC, there was another transaction from the same address, this time withdrawing 0.000137 ETH.
Approximately 1.5 hours following the second transaction, a substantial amount of around 9500 ETH was depleted from the vault.
Addresses labelled to the exploiter:
2️⃣ USDT:
At 6:30:11 PM UTC, the address identified as Orbit Bridge Exploiter 5 initiated the draining of 9.71 USDT from the Orbit Chain ETH vault. Shortly thereafter, at 7:51:35 PM UTC, a subsequent transaction of the same value occurred.

Approximately one and a half hours subsequent to the second transaction, the vault suffered a significant depletion, losing an estimated $30 million worth of USDT.
Addresses labelled to the exploiter:

3️⃣ USDC:
At 08:04:23 PM UTC, the address identified as Orbit Bridge Exploiter 1 initiated a withdrawal of 3.92 USDC from the Orbit Chain ETH vault. Approximately 1 hour and 20 minutes later, the vault experienced a significant depletion, losing around $10 million worth of USDC.
Addresses labelled to the exploiter:
4️⃣ DAI:
At 08:22:59 PM UTC, the Orbit Bridge Exploiter 3 address made an initial withdrawal of 1.322 DAI from the Orbit Chain ETH vault. Around 35 minutes later, the vault suffered a substantial depletion, losing roughly 10 million DAI.
Addresses labelled to the exploiter:

5️⃣ WBTC:
At 08:40:35 PM UTC, the Orbit Bridge Exploiter 2 address conducted an initial withdrawal of 0.012 WBTC from the Orbit Chain ETH vault. Around 30 minutes later, the vault was emptied of approximately 230.879 WBTC.
Addresses labelled to the exploiter:


What was the problem with code??
🎯Issue with withdraw() function :
The "withdraw" function's validation falls short in two crucial aspects: it lacks proper validation for the token parameter and fails to confirm the availability of the withdrawal amount (uint[0]) in the vault. Although the function performs checks on signatures, chain IDs, and used withdrawals, it overlooks essential verification steps.
// Fix Data Info
///@param bytes32s [0]:govId, [1]:txHash
///@param uints [0]:amount, [1]:decimals
function withdraw(
address hubContract,
string memory fromChain,
bytes memory fromAddr,
bytes memory toAddr,
bytes memory token,
bytes32[] memory bytes32s,
uint[] memory uints,
uint8[] memory v,
bytes32[] memory r,
bytes32[] memory s
) public onlyActivated {
require(bytes32s.length >= 1);
require(bytes32s[0] == sha256(abi.encodePacked(hubContract, chain, address(this))));
require(uints.length >= 2);
require(isValidChain[getChainId(fromChain)]);
bytes32 whash = sha256(abi.encodePacked(hubContract, fromChain, chain, fromAddr, toAddr, token, bytes32s, uints));
require(!isUsedWithdrawal[whash]);
isUsedWithdrawal[whash] = true;
uint validatorCount = _validate(whash, v, r, s);
require(validatorCount >= required);
address payable _toAddr = bytesToAddress(toAddr);
address tokenAddress = bytesToAddress(token);
if (tokenAddress == address(0)) {
if (!_toAddr.send(uints[0])) revert();
} else {
if (tokenAddress == tetherAddress) {
TIERC20(tokenAddress).transfer(_toAddr, uints[0]);
} else {
if (!IERC20(tokenAddress).transfer(_toAddr, uints[0])) revert();
}
}
emit Withdraw(hubContract, fromChain, chain, fromAddr, toAddr, token, bytes32s, uints);
}
The above mentioned "withdraw" function lacks critical validation:
It fails to validate the provided token parameter, enabling an exploiter to specify any token address for withdrawal without restriction.
It lacks a verification step to ensure that the uint[0] (amount) matches the actual vault balance of the specified token, risking withdrawals of unavailable funds.
Tokens are directly transferred based on supplied parameters without verifying if 'msg.sender' possesses proper authorization to withdraw that token and amount, creating a potential security loophole.
There's a failure to check if the Vault balances are sufficient, allowing withdrawals even if the balance is less than the specified withdrawal amount for the token.
Refining these aspects is crucial to fortify the security and integrity of the withdrawal process within the function.
This oversight permits the withdrawal of arbitrary amounts of any token, circumventing access controls and vault balance protections entirely.
This vulnerability is not isolated and can be systematically exploited, posing a severe risk of depleting the vault of multiple tokens. Exploitation of this flaw has led to the unauthorized withdrawal of substantial assets, including $30 million USDT, $10 million DAI, $10 million USDC, approximately 231 wBTC (valued at approximately $10 million), and 9,500 ETH (equivalent to approximately $21.5 million).
🎯Issue with _validate() function :
Based on the withdraw function's logic, the validatorCount parameter must be greater than or equal to the required index. This mechanism guarantees that the transaction can only progress if there are a sufficient number of valid signatures in place.
function _validate(bytes32 whash, uint8[] memory v, bytes32[] memory r, bytes32[] memory s) private view returns (uint) {
uint validatorCount = 0;
address[] memory vaList = new address[](owners.length);
uint i = 0;
uint j = 0;
for (i; i < v.length; i++) {
address va = ecrecover(whash, v[i], r[i], s[i]);
if (isOwner[va]) {
for (j = 0; j < validatorCount; j++) {
require(vaList[j] != va);
}
vaList[validatorCount] = va;
validatorCount += 1;
}
}
return validatorCount;
}
The _validate function indeed confirms the validity of signatures from recognized owners, but it lacks a direct correlation between signatures and transaction details in terms of the whash. This gap implies that if an attacker gains access to the private key of just one owner, they could generate valid signatures for any transaction. Because _validate doesn't validate the association of the signature with specific transaction details, these forged signatures would be deemed valid, opening the door to unauthorized transactions.
Technical cum Brief Explanation ➖
Attackers acquired a recognized validator's private key within the Orbit Chain system.
With this key, they generated valid signatures for transactions.
Exploiting the vulnerability in the
_validatefunction, which doesn't directly link signatures to transaction details (encapsulated inwhash), they bypassed this check.The
_validatefunction solely verified signature authenticity, not their association with transaction specifics.Leveraging this flaw, attackers executed these crafted transactions, leading to unauthorized withdrawals of significant assets from the vaults.
Orbit Chain confirms the exploit:
The orbit exchange team sent an on-chain message to the attacker, stating that they are open to suggestions and ready to listen.
Recent Update➖
Mitigation Steps➖
Addressing the various facets of the Orbit Chain incident involves enhancing blockchain security, smart contract design, and operational protocols. Key focal points revolve around bolstering validation integrity, safeguarding private keys, and instituting fail-safes against unauthorized transactions.
Valid Signature Misuse Mitigation: Implement multi-factor transaction validation. This entails linking each signature to specific transaction parameters and requiring secondary confirmation (e.g., off-chain verification or multi-signature requirements) to prevent single-key compromises.
Withdrawal Function Vulnerability: Enhance the withdrawal function by enforcing strict checks for token addresses and withdrawal rights. Use whitelists for approved tokens and implement role-based access control (RBAC) to authorize withdrawal requests from designated entities.
Anomaly Detection System: Integrate an automated system to identify unusual transaction patterns, such as large withdrawals in a short period. This system triggers a transaction pause for manual review, acting as an early warning mechanism to prevent substantial losses.
Key Management Best Practices: Employ hardware security modules (HSMs) for secure private key storage, reducing vulnerability to external breaches
What we do at DeHackAI ?

DeHack champions proactive defense in the Web3 realm, leveraging advanced technology for early vulnerability detection. Through meticulous code audits and AI-driven monitoring tools, vulnerabilities within smart contracts and protocols are identified and fortified preemptively. This proactive stance ensures resilience, preempting threats before they materialize, fostering a secure Web3 landscape built on trust and reliability for developers and users alike.
Join us in our mission to cover, protect, and secure on-chain digital assets.
Official Website: https://www.dehack.ai/
Twitter:https://twitter.com/DeHackAI